Necurs is the name of the botnet actively distributing malicious software. It used to spread the nasty infection Locky Ransomware, but this report is not about this case. Malware researchers working at the cybersecurity department noticed another flow of malicious emails sent by this botnet on November 30, 2017. These emails were spreading another ransomware infection called Globeimposter.
If the malicious attachment is opened by the user, the ransomware infection immediately infiltrates the computer and starts doing its job. It should be noted that crypto-malware is one of the most dangerous types of malware computer users can encounter these days, so its successful infiltration always results in certain losses. Usually, a bunch of personal files stored on compromised machines are damaged by the threat.
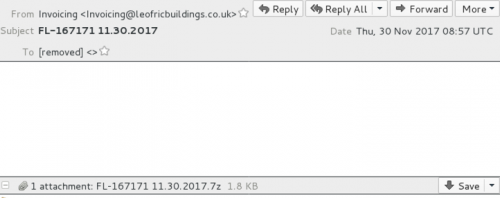
It should not be a huge problem to recognize emails delivering Globeimposter Ransomware now because it is already known how they look like. The first sign showing that the email received might contain a malicious attachment promoting the ransomware infection is the sender Invoicing in the From: line, for example, Invoicing <Invoicing@random company>. It should be noted that some of these companies whose names are used in malicious emails exist and some of them do not, but they surely have nothing to do with the malicious campaign. What else suggests that the email received is sent by the Necurs botnet promoting malware is the Subject line – FL-610025 11.30.2017 or Emailing-10006004318. Keep in mind that numbers used next to FL and Emailing are completely random and thus are subject to change. The third symptom showing that the email might be malicious is the empty body. It has been observed that emails the Necurs botnet sends to potential victims only contain a single attachment. The attachment itself does not look harmful at all at first glance. Specifically speaking, it is a harmless-looking .7z file with a size of 1.8 KB (it is subject to change too). Of course, it is not what it seems to be. In reality, it contains VBS files that are used to drop the Globeimposter Ransomware on victims’ machines.
When the malicious attachment is opened by the user, the automatic Globeimposter Ransomware download is triggered. Malware researchers say that the following domains (see below) might be involved in the distribution of this ransomware infection, so they should be blocked. It seems that some of these are legitimate domains hacked by cyber criminals.
- hxxp://accessyouraudience.com/JHGcd476334?
- hxxp://alucmuhendislik.com/JHGcd476334?
- hxxp://awholeblueworld.com/JHGcd476334?
- hxxp://bit-chasers.com/JHGcd476334?
- hxxp://datenhaus.info/JHGcd476334?
- hxxp://hexacam.com/JHGcd476334?
- hxxp://mh-service.ru/JHGcd476334?
- hxxp://yamanashi-jyujin.jp/JHGcd476334?
- summi.space
- n224ezvhg4sgyamb.onion.rip
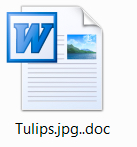
It is impossible not to notice the successful infiltration of Globeimposter Ransomware because it encrypts files it finds on compromised machines first things first and appends the .doc extension to the victims’ personal data.
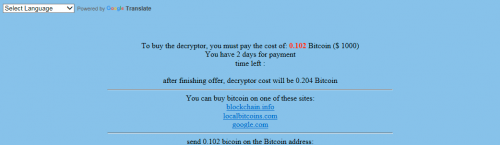
There is only one reason it does that – so that crooks would have a chance to obtain money from users. The ransomware infection does not try to hide its motives. The ransom note READ_ME.html demanding money is dropped on affected computers immediately after files are locked:
Ransomware infections affect the most valuable users’ files, including pictures, documents, videos, music, and other files, which is why so many victims make a decision to give cyber criminals what they want, i.e. to send money to them. It seems that money (0.102 Bitcoin) is not the only thing cyber criminals behind Globeimposter Ransomware want from users. They are also asked to enter the existing email address “to get the decryptor,”, but, according to researchers, this should not be done because these submitted email addresses might be used for other purposes too, for instance, to send malicious emails promoting other harmful infections to users again. You should not give any of these two things to crooks behind this malicious campaign no matter how badly you need to decrypt those affected files because there are no guarantees that the decryptor will be sent to you and you could unlock your files after you pay the ransom. Instead, use alternative data recovery methods, for example, all encrypted files can be restored from a backup. No matter what you decide, do not forget to delete the ransomware infection from the affected computer because it will keep working on it until you disable it yourself, meaning that it might encrypt all new files created too. The ransomware infection can be deleted manually (consult the manual removal guide provided below this article), or it can be erased with an automated malware remover. The most important thing is not to leave a single malicious file active on the system, so that the ransomware infection could not revive.
It is very likely that Necurs will be used to distribute other malicious applications in the future too, so users who do not want to become victims of dangerous malware again should carefully check all emails they are about to open and delete those sent from unknown senders right away – this is the major rule. Keep in mind that emails spreading malware might be very persuasive.
Delete Globeimposter Ransomware
- Launch Run (press Win+R).
- Type regedit.exe in the box and click OK.
- Go to HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce.
- Delete the Value associated with the ransomware infection.
- Close Registry Editor and open Windows Explorer.
- Remove all potentially malicious files downloaded recently.
- Empty Trash.
- Perform a system scan with a diagnostic scanner to check whether all malicious components have been erased.
References:
- Necurs Botnet Malspamming Globeimposter Ransomware via Fake Invoices. My Online Security. Keep yourself safe online
- Necurs Botnet Malspam Pushes Globeimposter Ransomware. Malware Traffic Analysis
- Necurs Botnet. Wikipedia