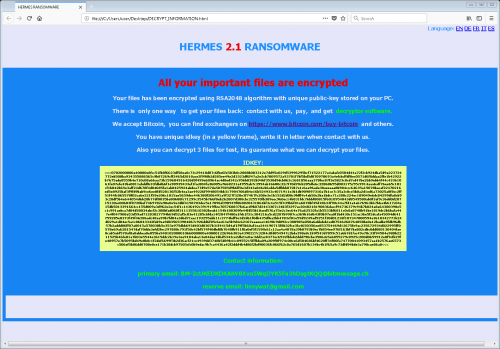
In early 2017, a new infection by the name Hermes Ransomware was discovered. A couple of months later, the infection was upgraded, and was operating as Hermes 2.0. The criminals behind the infection were clearly unsatisfied, as a new version, Hermes 2.1, was launched recently. It was discovered that the infection was distributed with the help of the so-called Greenflash Sundown Exploit Kit. Korea Computer Emergency Response Team (KrCERT) discovered earlier this year that a vulnerability (CVE-2018-4878) allowed to execute code in Flash Player remotely. The vulnerability was affecting Flash Player versions up to 28.0.0.137 version, and it was patched only on February 6th. The vulnerability was soon included in exploit kits, which meant that operating systems running unpatched Flash Players were at risk. One of the infections to exploit the vulnerability was Hermes 2.1 Ransomware.
According to the researchers at the “Malware don’t need coffee” blog, Greenflash Sundown is a version of the well-known Sundown exploit kit, whose last activity was recorded in 2017. The sun went down on this exploit kit when its source code was leaked online. The researchers also inform that the EK is exclusively used by the infamous ShadowGate Group. Greenflash Sundown quickly used the opportunity provided to them by the exploit to spread Hermes 2.1, and on February 27th, the infection started being spread via a compromised website. It is believed that the main target is South Korean users, and that the attacker operates from North Korea. Using the Flash Player zero-day, cyber criminals also have the opportunity to embed the Flash exploit to Microsoft Office documents that could be spread using spam emails. If the targeted victim was tricked into opening the file, the ransomware was launched on the system without the notice of the victim. The infection would then initiate the encryption of files, which was done using an AES encryption key silently downloaded from a remote server. The decryption key would be encrypted using an RSA key to ensure that it could not be deciphered.
When Hermes 2.1 Ransomware reaches its target location, it does not waste time to initiate malicious processes that lead to the encryption of files. Once they are encrypted, the unique “.hermes” extension is added to their names for easy recognition. After the attack, the threat creates a file called “DECRYPT INFORMATION.html,” which contains a message regarding the situation. When the victim opens the file, they are informed that they must pay for the so-called “decryption” software. The sum of the ransom is not revealed, and that is because the attacker wants the victim to establish communication first. The ransom note informs that they are to send a file named “UNIQUE_ID_DO_NOT_REMOVE” to BM-2cXfK4B5W9nvci7dYxUhuHYZSmJZ9zibwH@bitmessage.ch. The second address, x2486@india.com, is presented as the “reserve.” The infection is meant to back the victim into a corner, so that they could do nothing else but obey the demands made by the creator of Hermes 2.0. The problem is that the victim is unlikely to be presented with a decryptor if they paid the ransom in full. Most likely, if the ransomware encrypts files, recovering them is impossible unless a free decryptor is made publicly available.
Ransomware is powerful because it hits Windows users at their most vulnerable spot, which is their personal data. This particular infection does not affect the operating system or its functionality; although, it is possible that it could corrupt the files of downloaded software, which, of course, would make it impossible to run this it. While it should not be hard to reinstall software, recovering personal files might be impossible if backups do not exist. It is extremely important to discuss this because that is a versatile “remedy.” Computers go through technical damages. Computers get lost or stolen. Computers get invaded by malware that can take personal files hostage or delete them altogether. None of this is scary if files are backed up externally. It is important to back up files on external drives or online because backups offered by the system are not always safe. Even in this case, for example, Hermes 2.1 can delete backup files found on the system. If you need advice on how to back up your personal files, use the comments section to start a discussion.
While having backup copies of the personal files can save the victims of ransomware from a lot of trouble, they cannot save them against the invasion of malware. Vulnerabilities cannot be avoided, and exploits preying on them will continue being created and used for the benefit of malicious parties. This is why it is crucial that everyone takes appropriate security measures. Of course, it is up to service providers (e.g., Adobe, who is responsible for making Flash Player safe) to ensure safety, but there are things that everyone can and should do. First and foremost, legitimate and up-to-date security software must be installed and must run at all times. Second, ALL security updates must be downloaded as soon as they come. If an update is skipped, a vulnerability might be exposed, and it is only a matter of time before it is exploited.
How to set up Automatic Updates on Windows
Windows 10
- Click the Windows Start button and select Settings.
- Move to Update & security and then click Windows Update.
- Select Advanced options.
- Adjust the settings to ensure that they updates are installed automatically.
Windows 8/Windows 7
- Simultaneously tap Win+E to launch Explorer.
- Enter Control Panel\System and Security into the bar at the top.
- Click Windows Update and select Change settings.
- Adjust the settings to ensure that they updates are installed automatically.
References
Fearn, N. February 2, 2018. Adobe acknowledges Flash zero-day that’s been exploited since November. The Inquirer.
Kafeine. March 9, 2018. CVE-2018-4878 (Flash Player up to 28.0.0.137) and Exploit Kits. Malware don’t need coffee blog.
KrCERT. January 31, 2018. Adobe Flash Player 신규 취약점 주의 권고. KrCERT.
Malwarebytes Labs. March 14, 2018. Hermes ransomware distributed to South Koreans via recent Flash zero-day. Security Boulevard.