Cyber criminals have found a new way to distribute the nasty infection GandCrab Ransomware, meaning that the number of users who encounter this threat might continue growing. Luckily, BitDefender has released a free decryptor that can be used to unlock files affected by this threat. A new tactic used to spread this infection involves the “The HoeflerText font wasn’t found” scam. Malware researchers came across this scam at the beginning of 2017 for the first time. At that time, it promoted another harmful malicious application Spora Ransomware and Fleercivet Trojan. The scam targets Google Chrome users primarily, but Mozilla Firefox users should be cautious too because a similar scam “Hoefler text font wasn’t found” might trick them into installing Mozilla Font Pack which carries Zeus Panda, a banking Trojan.
Researchers at NeoSmart Technologies have observed that GandCrab Ransomware is primarily distributed via legitimate but compromised websites. Specifically speaking, these websites contain a malicious JavaScript code inserted by the attacker. The malicious script modifies the text rendering on hacked websites, so what users see when they visit them is scrambled content consisting of random symbols and various random characters. According to specialists, the majority of users end up on these compromised websites and encounter the “The HoeflerText font wasn’t found” scam because they mistype URLs of websites they want to visit or get redirected to them against their will after clicking on a malicious link/pop-up.
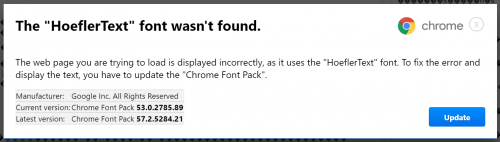
Once the user ends up on a hacked website, the script makes the website unreadable and displays a pop-up claiming that the issue can be fixed by simply installing the HoeflerText Font. The text of the scam can be found below:
The “HoeflerText” font wasn’t found.
The web page you are trying to load is displayed incorrectly, as it uses the “HoeflerText” font. To fix the error and display the text, you have to update the “Chrome Font Pack.”
Manufacturer: Google Inc. All Rights Reserved
Current version: [software version]
Latest version: [software version]
The “The HoeflerText font wasn’t found” scam is extremely appealing, so it is not surprising that so many computer users fall for it. It not only contains the Chrome logo in the top-right corner, but also uses the right shade of blue on the button it contains.
If the user falls for the scam and clicks the Update button on the fake pop-up window, the download of Font_Update.exe begins. This is an executable of the g.js script. Once this file is executed, the script connects to the C&C server and starts downloading necessary files automatically. It, first, downloads the NetSupport Manager, which is, in fact, legitimate software. Then, once all files are downloaded, client32.exe is used to upload GandCrab Ransomware to victims’ computers.
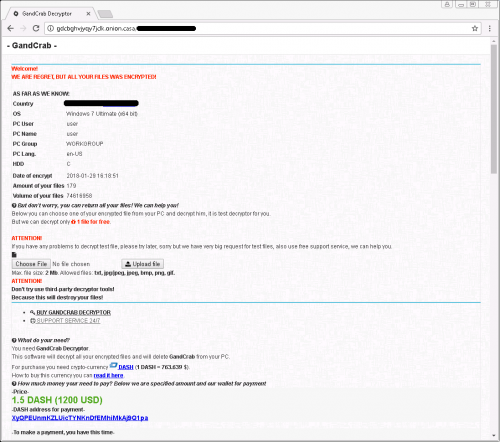
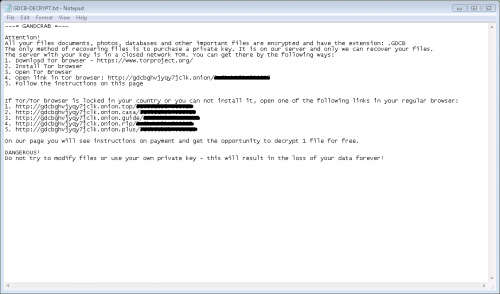
GandCrab Ransomware is a nasty crypto-threat coded in C++. It does not differ much from other sophisticated ransomware infections because it also locks files found on affected computers with the strong AES (Advanced Encryption Standard) cipher. It targets hundreds of files users consider valuable, including those containing such popular extensions as .ppt, .re4, .zip, .xlm, .gry, .cpi, .fla, .mpg, .pub, .java, .jpeg, .mp4, and .mp4. Once it encrypts users’ files, they all get the .GDCB extension appended to them. The ransomware infection also terminates certain processes (e.g. wordpad.exe and synctime.exe) on victims’ computers and drops a ransom note CDCB-DECRYPT.txt once it successfully locks victims’ files. Surprisingly, GandCrab Ransomware does not demand a ransom in Bitcoin. Users are asked to send 1.5 DASH (~1200 USD) to get files decrypted. If the ransom is not paid in 4 days and 12 hours, the decryption price doubles. Since there are no guarantees that users could unlock their files after sending money to cyber criminals, they should not transfer the ransom. In any event, the ransomware infection must be deleted from affected computers as soon as possible.
The “The HoeflerText font wasn’t found” scam is, without a doubt, not the only scam that might be used to trick users into installing malicious software, so users should not keep their computers unprotected. Also, they should be more attentive since it might be possible to recognize the scam. First, always check whether the version of your browser matches the version indicated on the pop-up displayed to you. If they differ, it means that the pop-up you use is a pure scam. Second, if the pop-up you see does not have X, i.e. it cannot be closed normally, the chances are high that it is fake and only seeks to convince you to click the button it contains. Last but not least, if you notice after you click the Download button the pop-up contains that the download does not have a file icon, cancel the download process immediately. If the browser with the fake pop-up cannot be closed in a usual way, it does not mean that it cannot be dismissed – kill the process of the web browser via Task Manager.
References:
- Al-Qudsi, M. Beware of this new Chrome “font wasn’t found” hack! NeoSmart Technologies Blog
- EiTest campaign Hoefler Text Pop-up delivers GandCrab Ransomware. Broadanalysis
- Fortuna, A. The ‘HoeflerText’ font wasn’t found? Beware, it’s a trap! Andrea Fortuna Blog
- Kumar, M. Beware! Don’t Fall For “Font Wasn’t Found” Google Chrome Malware Scam. The Hacker News