Do you know what Spora Ransomware is?
New Year comes with new sophisticated ransomware that might give you a good run for your money. Spora Ransomware was first detected on January 10th, 2017, and this program is very likely to cause a lot of trouble for computer users worldwide. In order to protect yourself from this infection, you have to know the main ransomware distribution patterns that could be employed to compromise your computer. Also, you should consider acquiring a licensed antispyware tool that would safeguard your system from various threats. Finally, if you have been infected with this program, you should remove Spora Ransomware immediately following the instructions below this description.
Our research lab team suggests that Spora Ransomware is a Russian infection because the word “Spora” in Russian means “spore.” Therefore, it might seem that the distribution and the infection methods used by this program are somewhat similar to how various types of plants employ spores to reproduce. The thing that really makes this program stand out from all the other ransomware infections we have encountered so far is its ability to work offline. The program does not generate any network traffic, and it also boasts of solid encryption and a sophisticated ransom payment website. All these features allow us to assume that the program is fully and thoroughly developed.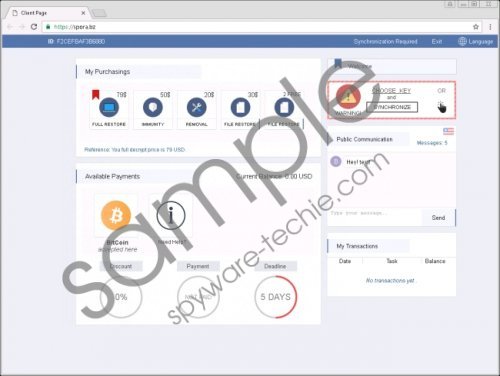 Spora Ransomware screenshot
Spora Ransomware screenshot
Scroll down for full removal instructions
On the other hand, Spora Ransomware employs the most common ransomware distribution method: spam emails. That is why we said users should know how ransomware spreads if they want to avoid these infections. The messages that spread the infection around usually look like invoices from various online stores. The attached installer file looks like a .zip document. Once the user downloads and unzips the file, they find another file in it, and this file has the .hta extension (an HTML application). The double extension the installer file has is there to trick the unsuspecting users that the file they are about to open is absolutely safe.
However, once you launch the malicious file, Spora Ransomware creates a couple of executable files (with the .exe extension). These files could be dropped in various directories in your system, and during our test, the malicious files were dropped on the Desktop and the %HOMEDRIVE% directory. However, our team points out these files may not be responsible for encrypting your files. The file that does that is most likely located in the %TEMP% directory, although the location could vary from computer to computer. You will find the list of all the potential locations at the bottom of this article.
Different ransomware infections target a different number of file extensions, and this new infection does not have a long list, but you can be sure that it will encrypt all of your most-commonly used files. Spora Ransomware also makes sure that your computer would still be operational after the encryption, so it leaves out the files that contain the following strings: “games,” “program files (x86),” “program files,” and “windows.” Thus, the files in the directories with the aforementioned strings will not be affected by the encryption.
Another thing that puts Spora Ransomware apart from other similar ransomware programs is that this infection does not add any kind of extension to the encrypted files. Therefore, it might be harder for a user to distinguish between encrypted and healthy files. But perhaps that is done on purpose, so that users would swarm into the ransomware website for the decryption key. The website itself is very well-developed, and it even offers a service menu where a user can choose between:
-
FULL RESTORE – 79$
-
IMMUNITY – 50$
-
REMOVAL – 20$
-
FILE RESTORE – 30$
-
FILE RESTORE – 2 FREE
Since the infection is really new, there is still no public decryption tool available, but that does not mean you should hurry and give your money away to these cyber criminals. As our research shows, currently, Spora Ransomware targets only computer users in Russia, but it is very likely that the infection will soon spread to other countries, too. Every year, dangerous and sophisticated programs show up in January, so we believe that Spora Ransomware is here for a long run.
Please follow our instructions to remove Spora Ransomware from your computer. If find the instructions too long, and the manual removal is too tedious of a process for you, please refer to a licensed antispyware tool that will delete the infection for you automatically.
How to Remove Spora Ransomware
- Remove the malicious file* from your Desktop.
- Press Win+R and type %AppData%. Click OK.
- Find and remove the malicious file from the directory.
- Repeat steps 2 and 3 for these directories: %TEMP%, %HOMEDRIVE%.
- Use Win+R to access various directory and delete the following files:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\[Unique ID].HTML
%APPDATA%\Microsoft\Windows\Templates\[Unique ID].HTML
%APPDATA%\Microsoft\Windows\Templates\[Unique ID].KEY
%APPDATA%\Microsoft\Windows\Templates\[Unique ID].LST
%APPDATA%\[Unique ID].HTML
%APPDATA%\[Unique ID].KEY
%APPDATA%\[Unique ID].LST
%USERPROFILE%\Desktop\[Unique ID].HTML
%USERPROFILE%\Desktop\[Unique ID].KEY
* The file will most likely have a random 10-digit name. It could also have a random CLSID name (XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX.exe).
In non-techie terms:
Spora Ransomware is a program that comes ready to rip you off, and it does that in style. It is obvious that you should never pay anything to the people behind this infection. Instead, get yourself a powerful computer security tool that will remove Spora Ransomware for you, and you will never have to worry about this infection again.
As for your files, you should consider restoring them from a system backup (like an external hard drive), but you should only do that when you have the program removed.
