Do you know what Locky Ransomware is?
Locky Ransomware is a nasty Trojan that settles in computers with the help of the user. As it enters your system, it encrypts most of your files, especially the personal ones such as photos, videos, various documents, etc. Meaning that you will not be able to do anything with the encrypted files, unless you get a unique decryption key. As a result, you are asked to pay the ransom in exchange for the decryption key. However, we advise you to think about this carefully, because even if you do as these cyber criminals ask, there is no assurance that they will help you regain your files. Before you decide, you could read this article and learn more about this malware. Also, if you choose to remove this ransomware, you should follow our prepared instructions as Locky Ransomware files must be deleted in a particular sequence.
As we mentioned before, this Trojan could not get in without your help. However, there is no doubt that you were tricked and did it unknowingly, because this malware spreads through email attachments. At first, users receive an email message with the attachment of Microsoft Word document and, as they open it, they activate a downloader that drops Locky Ransomware in their computer. Afterwards the malware encrypts all files that have these extensions: .mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat. As you see the list of file types is very wide and so all your data will be encrypted for sure. Locky Ransomware uses the AES encryption method which is used worldwide for non-malicious reasons too.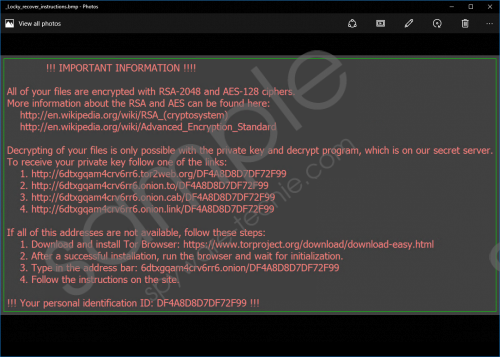 Locky Ransomware screenshot
Locky Ransomware screenshot
Scroll down for full removal instructions
Our researchers tested this Trojan in our internal lab and found out that Locky Ransomware does not lock your screen like other similar infections, but it changes your desktop picture with the message that explains the situation and tells you what you must do. The same message is displayed in a Notepad file that is added to every location where your files are encrypted. Though the message only describes you how to find the rest of instructions for payment. It says that you must follow one of the provided links, e.g. this is one of them 6dtxgqam4crv6rr6.onion.cab/2CA991DE4913366C. The instructions on the site will demand 0.5 bitcoins from you and explains how to get them. Also, you would need a unique identification ID from random sixteen digits that was given to you in the message. Unfortunately, the ransomware deletes all Shadow copies so all that remains are unusable encrypted files and there is no way you could decrypt them without the unique decryption key. It is up to you if you want to pay the ransom, but 0.5 bitcoins are quite a huge amount of money for a service with no guarantee. It all happens suddenly, but still you should think about it for a couple of minutes and decide if your files are really lost, because you might have some copies on other devices.
Since you cannot be sure if you will get the mentioned decryption key after paying the ransom, we would advise you not to give in and remove the malware at once, especially if your encrypted files are not something you could not live without. If you decide to erase Locky Ransomware you should know that there are two possible options, either you do it manually or automatically with a legitimate antimalware tool that would also protect your computer in the future. Be aware that if you choose to get rid of it manually, you should follow our provided removal instructions because it is important to delete a particular file first and then remove the others.
Delete Locky Ransomware manually
- Press Windows Key+R to launch the RUN.
- Insert this location: %Temp%
- Locate the executable file named svchost.exe.
- Right-click on it and press Delete.
- Locate file titled _Locky_recover_instructions.bmp on your desktop.
- Right-click on it and select Delete.
Remove the Locky Ransomware created Windows Registry keys
- Launch the RUN (Windows Key+R).
- Type regedit and press OK.
- Navigate to: HKCU\Software\Locky.
- Right-click on the Locky key and click Delete.
- Locate this path: HKCU\Control Panel\Desktop.
- Find the key named Wallpaper "%UserProfile%\Desktop\_Locky_recover_instructions.bmp".
- Right-click on it to Delete it.
- Navigate to: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers.
- Find and delete Value BackgroundHistoryPath0 on the right side.
- Empty your Recycle Bin.
- Restart your computer.
In non-techie terms:
Locky Ransomware is an infection that you could have avoided. As for the future, you should be more careful while opening email attachments and it would be better to ignore any documents that look suspicious or unfamiliar. In fact, you could easily protect your computer from such dangerous infections with a legitimate antimalware tool that would warn you about harmful attachments.
