Do you know what Cerber Ransomware is?
We want to inform you about a new cyber threat called Cerber Ransomware. Our malware analysts were able to obtain a working sample of this infection and test it. The results were rather alarming, and therefore, we recommend that you remove this ransomware from your PC as soon as possible. Unfortunately, if your computer becomes infected with this ransomware, then it will encrypt certain file formats and their decryption requires a key that you can only get after paying a hefty ransom fee. However, there is no way of knowing whether this ransomware’s developers will provide you with this key. And, to our knowledge, there is currently no third-party tool that could crack Cerber Ransomware’s encryption.
Our researchers have received information which says that this ransomware is most likely distributed via a clandestine Russian forum that is inaccessible to the general public and only those who are a part of the tightly-knit hacker community have the possibility to acquire it. Furthermore, it is believed that this ransomware has been marketed as Ransomware as a Service (Raas) which means that its developers make money off other criminals who pay to use it. Therefore, Cerber Ransomware can become a significant problem and given that it is a service to be used freely; there is just no way to determine how it is distributed. We can only mention the methods that are used most often. These methods include sending email spam that contains a self-extracting archive, bundling it with pirated software, and promoting it via a fake Java update message that you may come across while surfing online. All in all, the possibilities are endless. Cerber Ransomware’s distribution methods are limited only by its user’s imagination.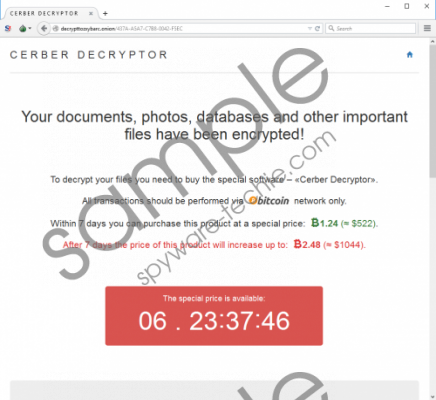 Cerber Ransomware screenshot
Cerber Ransomware screenshot
Scroll down for full removal instructions
Oddly enough, this program works only in specific countries and even if it infects a computer in a blacklisted country it will terminate itself. The list of countries in which Cerber Ransomware does not work are Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan. However, if your computer is not stationed in the aforementioned countries, then this ransomware can install itself in %AppData%\{RANDOM CLSID}. Its main executable file is also randomly named. After the files have been dropped, this infection will force reboot your computer in Safe Mode with Networking. Furthermore, it will configure itself to start each time you boot up your computer and execute every minute. Cerber Ransomware is set to generate a fake system message “You are about to be logged off” and it will stay there until you click Close and allow your PC to restart. Then it will reboot in normal Windows mode and initiate the encryption process.
This infection will scan your computer’s hard drive for certain files extensions. It has been configured to encrypt files that are not required for the operating system to run because otherwise your computer might not even boot up. It encrypts file formats that are used for storing personal information, such as ".7z", ".7zip", ".accdb", ".mp3", ".mp4", ".mpg", ".ptx", ".qbb", ".xlm", ".xlr", ".xlsm", and so on. In all, this ransomware is capable of encrypting more than 380 file formats. After encrypting a file, it will add its extension. For Example, the.docx extension in document.docx will be replaced with .CERBER (document.CERBER.) However, it will skip files located in the following locations:
- C:\$recycle.bin\
- C:\$windows.~bt\
- C:\boot\
- C:\drivers\
- C:\program files\
- C:\program files (x86)\
- C:\programdata\
- C:\users\all users\
- C:\windows\
- C:\Users\{User}\AppData\Local
- C:\Users\{User}\AppData\LocalLow
- C:\Users\{User}\AppData\Roaming
- C:\Users\Public\Music
- C:\Users\Public\Pictures\Sample Pictures
- C:\Users\Public\Videos\Sample Videos
- C:\tor browser\
After the encryption is complete, Cerber Ransomware will create three files on your desktop and in every folder in which it encrypted a file. These three files are named DECRYPT MY FILES.html, DECRYPT MY FILES.txt, and DECRYPT MY FILES.vbs. These files contain information about what has happened in case you did not release that your PC has been infected with ransomware. Furthermore, these files contain links to a Tor decryption service where you ought to pay the hefty 1.24 bitcoins ($500 USD) ransom fee.
These files also contain a link to the decrypttozxybarc.onion Tor site. This site functions as the channel paying the ransom and supposedly providing you with the decryption key. In theory, after you pay the ransom this website should provide you a download link to the decryption key. Cerber Ransomware uses the AES-256 cipher to encrypt the files and the RSA-576 cipher to encrypt the encryption key. RSA-576 is a rather weak encryption method, but, to date, there is no way to decrypt infected files using third-party tools, but hopefully, someone will come up with a way to do it.
In the meantime, all we can offer you is to remove Cerber Ransomware and try to restore the encrypted files from backup drives. Now, there are two ways you can delete this infection. We recommend using SpyHunter if manual removal proves difficult or unsuccessful. However, if you want to remove it manually, then use the instructions that we have provided below.
Boot up your PC in Safe Mode with Networking
Windows 8/8.1
- Simultaneously press Windows Key+C, and then click Settings.
- Click Power, hold down Shift on your keyboard and click Restart.
- Select Troubleshoot and go to Advanced options, and then select Startup Settings.
- Click Restart and press 5 on your keyboard to Enable Safe Mode with Networking.
Windows 7/Vista
- Open the Start menu and click the arrow next to the Shut Down button.
- Click the Restart button.
- Press and hold the F8 key as your computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking and press Enter.
- Log on to your PC with administrator rights.
Windows XP
- Open the Start menu and click Restart.
- Press and hold the F8 key while the computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking and press Enter.
- Log on to your PC.
Option one: manual removal
Remove the Point of Execution
- Press Windows+R keys on your keyboard.
- Type regedit in the resulting dialog box and click OK.
- Find and delete the String and Binary values that have %AppData%\{RANDOM CLSID}\*.exe Value data in the following registry keys.
- HKCU\Control Panel\Desktop|SCRNSAVE.EXE|
- HKCU\Software\Microsoft\Command Processor\AutoRun
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
*The executable file name is random
Delete malicious files
- Press Windows+E keys on your keyboard.
- In the resulting Explorer window’s address box enter the following directories and delete them.
- %ALLUSERSPROFILE%\Start Menu\Programs\*.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\*.lnk
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs\*.lnk
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\*.lnk
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\*.lnk
- "%AppData%\{RANDOM CLSID}\*.exe
Option two: automatic removal
- Go to http://www.spyware-techie.com/download-sph
- Download SpyHunter-Installer.exe
- Run the installation Wizard.
- Once installed, launch the program.
- Perform a full system scan.
- Click Fix Threats.
*The file name is random
In non-techie terms:
Cerber Ransomware is a malicious infection that has been configured to encrypt your personal files and demand that you pay $500 in exchange for the required decryption key. Unfortunately, currently, there is no way to decrypt the encrypted files using third-party software. However, we do not recommend paying the ransom since you might not get the decryption key. So in order to use your computer you have to remove this ransomware.
